Zero Trust SecOps service design
Reducing risk at U.S. Centers for Medicare and Medicaid
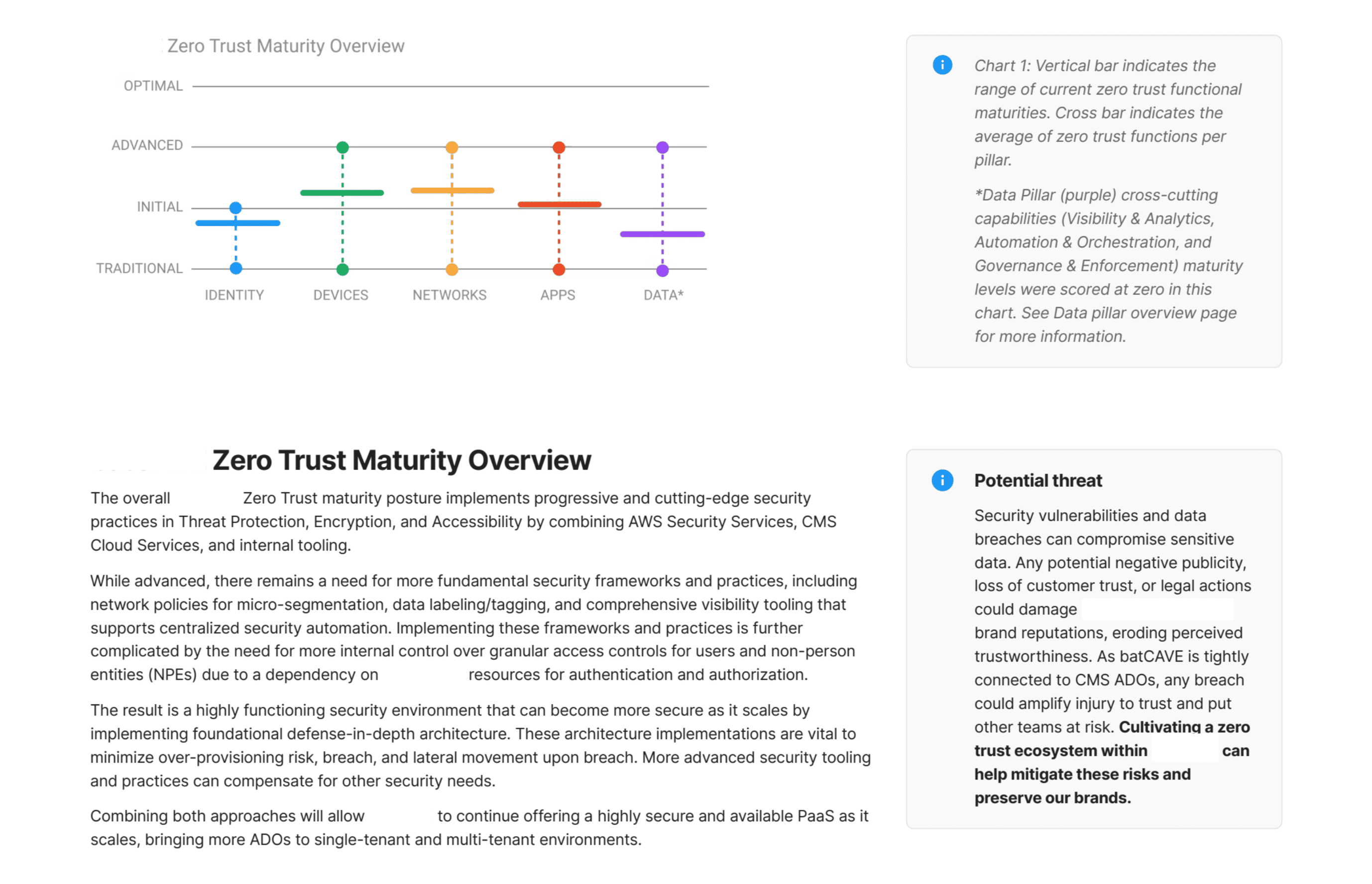
Outcomes
Americans protected by higher application security
Developer teams engaged
%
Control statements addressed
%
Security posture increase
Bonus Material
To socialize Zero Trust we create a typefont-based logo allowing us to embed branding across developer platforms and input devices. Whether in a polished presentation deck or in an ASCII-compatible line of code commented out, the Zero Trust initiative leaces its brand mark in line. The logotype conveys all three aspects of people, platform, and playbook. Reading as a fictional code command, an operation, and as a face.
ZERO(/}TRUST
ZERO(/}TRUST
Observe
Case Context
The client business unit is an IT department that provides cloud-based and on-premise infrastructure for 200+ application developers to build their apps on. These are applications that serve end users, medical providers, health systems, drug and appliance manufacturers, and benefits providers. Many applications contain personal identity and health information and are required to meet the highest standards of safety and accountability. Federally-mandated security protocols are recently required to update to the principles of Zero Trust.
The IT office works closely with governance, finance, and communications offices to serve an ecosystem of app developers. Developer teams along with many components of the offices are comprised of a mix of federal employees and contractors. Organizational complexity combined with multiple overlapping contract conditions create an environment that requires robust networking, planning, and communication to succeed.
Zero Trust is a countercurrent to traditional perimeter-based security practices. Published Cybersecurity and Infrastructure Security Agency (CISA) guidance helps us get better at employing accurate, least privileged, per-request access in information systems and services facing a network assumed to be compromised. This guidance means that every resource should be untrusted until proven otherwise. Most of what’s published on Zero Trust Architecture (ZTA) dives into the technical requirements and engineering processes that flow toward a given Zero Trust Maturity (ZTM) while offering instruction on what it may take to reach the successive maturity level.
Stakeholders
Application development teams, compliance managers, IT business unit.
Role
Service Design Strategist, Information Systems Technology
Collaborators
Security Architect, Security Engineers, Governance Experts, Business Owner, Component Director
Reflect
Design Principles
We group efforts into three areas of exploration.
People: The solution starts with the people who make it happen.
Platform: Solutions need to map to existing system opportunities and limits.
Playbook: Any intervention should be clearly documentable and explained.
Stakeholder engagement is paramount to getting any large-scale systems changes implemented. We conduct detailed customer and stakeholder scenarios to identify those areas with the highest risk and lowest barrier to change for quick wins and demonstration of concept. We roadmap the beadth of the project with editable service blueprints for agile iterative operations.
Methods
- Stakeholder map
- User interviews and ride-along
- Archetypes and Personas
- Cluster analysis
- Data mining
- Service blueprint
- Gap Analysis
- Value feasibility analysis
- Stakeholder training
Software
Figma, Coda, Confluence, Jira, Dovetail, Contentful, Mural, Miro, Kumu, Excel
Act
Implementing Zero Trust principles with existing SecOps is not a monolithic operation but an ongoing and, often, a zigzag process involving identity, infrastructure, networking, applications, and more. It quickly becomes evident that moving toward a Zero Trust Architecture (ZTA) requires cross-functional, interdisciplinary collaborations between DevSecOps experts, governance specialists, and business process influencers.
Samples
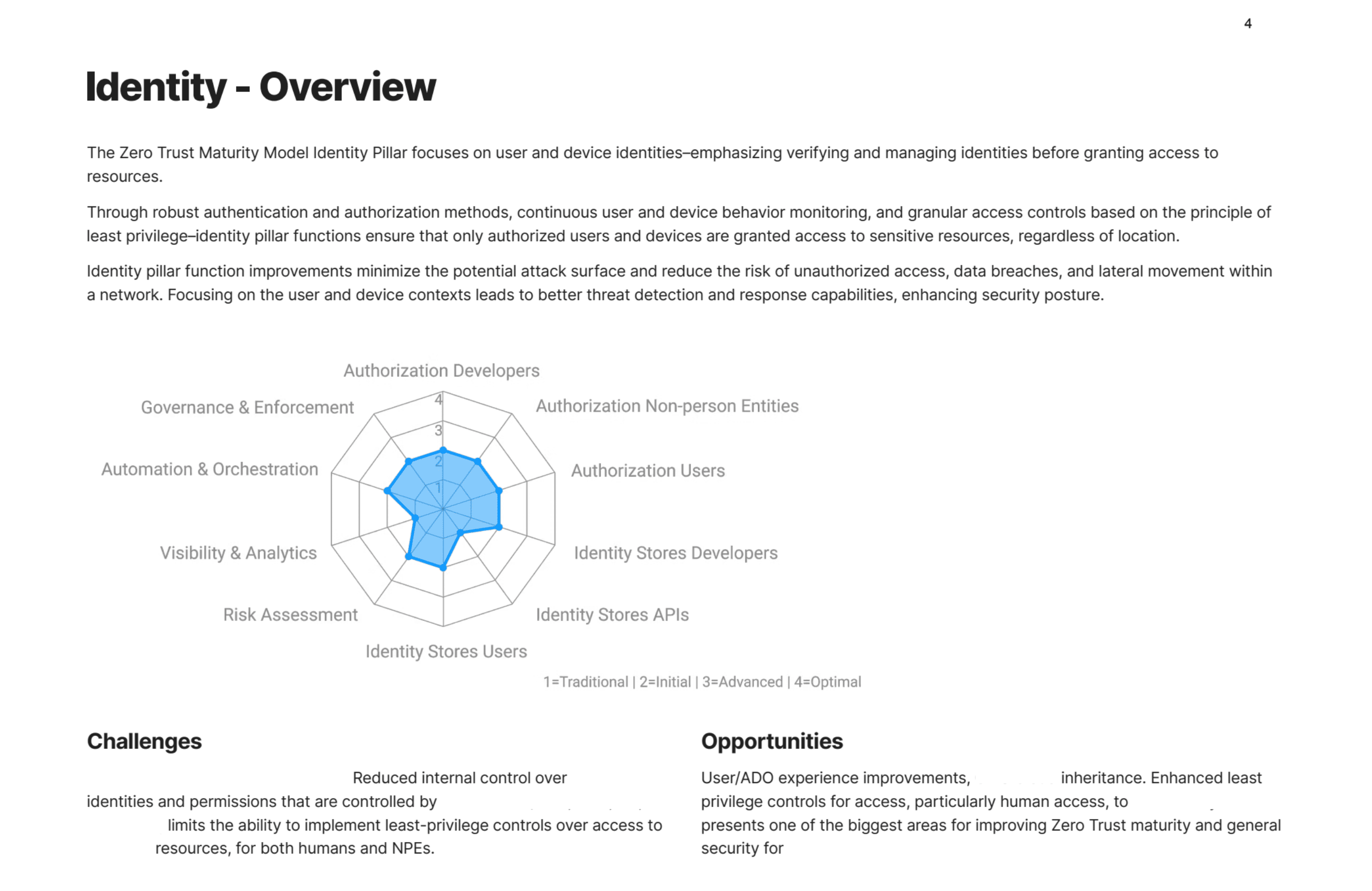
System diagram, people, technology, & zero trust principles.
This map brought systems-level thinking to the various stakeholders allowing quick visualization of the many system influences. Teams were able to find the right people, make informed decisions, ultimately resulting in more comprehensive, deliberate, and precise implementation of Zero Trust principles and practices.